Voice over Internet Protocol, which offers flexible and reasonably priced communication options, has changed communication in the digital age. However, there are security risks associated with this technological progress. An essential component of controlling and safeguarding VoIP communications is the Session Border Controller (SBC). This blog post explores the critical security improvements for your VoIP SBC, recommends effective VoIP security solutions, and gives developers thorough approaches to strengthen their systems.
Why VoIP Security Matters?
VoIP security is crucial because VoIP networks are vulnerable to threats like eavesdropping, denial of service (DoS) attacks, and toll fraud. Compromised VoIP systems can result in financial losses, legal repercussions, and damage to an organization’s reputation. Implementing advanced VoIP security solutions helps protect against these threats and ensures that communication remains safe and reliable.
Common VoIP Security Threats
Here are various security threats associated with VoIP, highlighting the essence of robust security measures to safeguard VoIP systems.
1. Eavesdropping
Eavesdropping is one of the most prevalent threats in VoIP communications. Unauthorized parties can intercept VoIP calls, exposing sensitive information. Implementing encryption protocols such as Secure Real-Time Transport Protocol (SRTP) is crucial in preventing eavesdropping and ensuring secure VoIP communication.
2. VoIP Phishing (Vishing)
VoIP phishing, or vishing, involves fraudulent attempts to obtain sensitive information through VoIP calls. Attackers often pose as legitimate entities to trick users into revealing personal or financial information. Educating users about recognizing phishing attempts and implementing caller ID verification can mitigate this threat.
3. Denial of Service (DoS) Attacks
DoS attacks aim to disrupt VoIP services by overwhelming the network with excessive traffic. This can result in degraded call quality or complete service unavailability. Deploying a robust VoIP Session Border Controller (SBC) can help manage and filter traffic, protecting the VoIP infrastructure from DoS attacks.
4. Call Fraud
Call fraud involves unauthorized use of VoIP services to make long-distance or premium-rate calls, leading to financial losses. Implementing strict authentication mechanisms and monitoring call patterns can help detect and prevent call fraud. Utilizing SBCs with fraud detection capabilities can further enhance security.
5. Malware and Viruses
VoIP systems are vulnerable to malware and viruses that can compromise the integrity of communications. Ensuring that all VoIP devices and software are updated with security patches is essential in preventing malware infections. Additionally, using reputable VoIP providers with robust security measures can provide extra protection.
With the increasing reliance on VoIP phone systems for business and personal communication, protecting these systems from security threats is paramount. A secure VoIP provider can offer peace of mind, ensuring that communication remains confidential and reliable.
🛡️ Secure your VoIP infrastructure before threats find you.
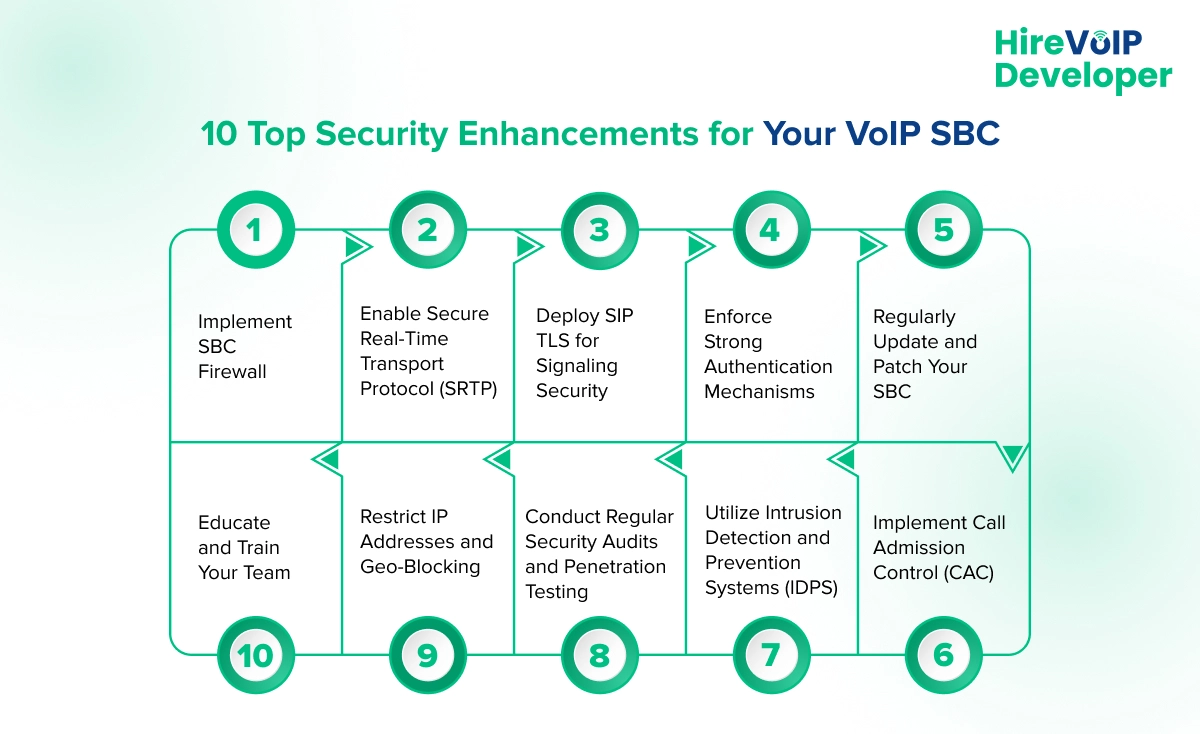
10 Top Security Enhancements for Your VoIP SBC
The increasing reliance on VoIP phone systems underscores the importance of securing VoIP infrastructure. As a VoIP Developer or a secure VoIP provider, ensuring robust security measures in your VoIP Session Border Controller (SBC) is critical. Below are ten top security enhancements to fortify your VoIP SBC.
1. Implement SBC Firewall
An SBC firewall is the first defense against unauthorized access and potential VoIP security threats. By filtering incoming and outgoing traffic, it ensures that only legitimate data packets reach your VoIP infrastructure.
2. Enable Secure Real-Time Transport Protocol (SRTP)
Encrypting voice data using SRTP helps protect against eavesdropping and interception. This protocol secures the media streams, ensuring that voice communications remain confidential.
3. Deploy SIP TLS for Signaling Security
Transport Layer Security (TLS) encrypts SIP signaling, preventing man-in-the-middle attacks. It ensures that call setup and teardown messages cannot be intercepted or tampered with.
4. Enforce Strong Authentication Mechanisms
Utilizing robust authentication protocols, such as two-factor authentication (2FA), strengthens access control and reduces the risk of unauthorized users entering VoIP phone systems.
5. Regularly Update and Patch Your SBC
Keeping your SBC firmware and software up-to-date is crucial. Regular updates and patches address vulnerabilities and protect against new threats, ensuring your VoIP infrastructure remains secure.
6. Implement Call Admission Control (CAC)
CAC helps manage bandwidth and prioritize critical calls, reducing denial-of-service (DoS) attack risk. It ensures the network can handle the volume of VoIP traffic without compromising security.
7. Utilize Intrusion Detection and Prevention Systems (IDPS)
IDPS monitors network traffic for potential threats and suspicious activity. Implementing these systems helps detect and prevent security breaches in real-time, safeguarding your VoIP infrastructure.
8. Conduct Regular Security Audits and Penetration Testing
Frequent security audits, VoIP quality testing, and penetration testing help identify vulnerabilities and weaknesses in your VoIP SBC. Addressing these issues promptly enhances the overall security posture of your VoIP systems.
9. Restrict IP Addresses and Geo-Blocking
Limiting access to trusted IP addresses and implementing geo-blocking can prevent unauthorized access from high-risk regions. This targeted approach enhances the security of your VoIP infrastructure.
10. Educate and Train Your Team
It is vital to ensure that your team understands the importance of VoIP security and follows best practices. Regular training sessions keep everyone informed about the latest threats and security measures.
Incorporating these top security enhancements in your VoIP Session Border Controller significantly mitigates the risk of VoIP security threats. Whether you’re a VoIP Developer or a secure VoIP provider, prioritizing these measures ensures a robust and secure VoIP infrastructure. Stay proactive and vigilant to maintain the integrity and confidentiality of your VoIP communications.
10 Best Practices for VoIP Security
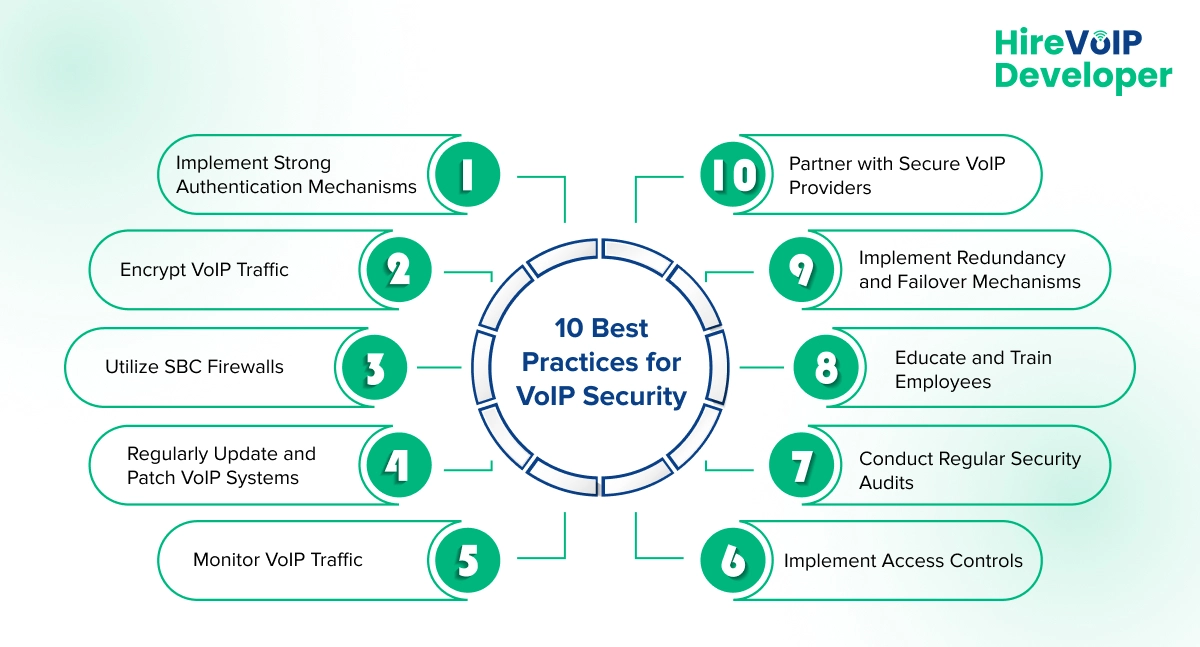
Here are the best practices for securing your VoIP infrastructure, safeguarding against potential threats, and ensuring seamless and secure communication.
1. Implement Strong Authentication Mechanisms
Robust authentication protocols are fundamental to preventing unauthorized access to VoIP systems. Multi-factor authentication adds a security layer by requiring multiple verification forms before granting access. VoIP developers should ensure robust authentication methods to protect against unauthorized usage.
2. Encrypt VoIP Traffic
Encryption is a major component of VoIP security. Secure Real-Time Transport Protocol (SRTP) is commonly used to encrypt voice data, ensuring that conversations remain private and tamper-proof. Implementing SRTP helps protect against eavesdropping and data interception, making it a vital security measure for secure VoIP providers.
3. Utilize SBC Firewalls
SBC firewalls act as a first line of defense against cyber attacks. They monitor and control the flow of VoIP traffic, blocking malicious activities and unauthorized access. VoIP SBCs with integrated firewall capabilities provide an additional layer of protection, ensuring that only legitimate traffic can access the network.
4. Regularly Update and Patch VoIP Systems
VoIP infrastructure should be regularly updated to protect against known vulnerabilities. Software patches and updates address security flaws and enhance the overall security posture. Regular maintenance and updates are essential to mitigate the risk of exploitation by cybercriminals.
5. Monitor VoIP Traffic
Continuous monitoring of VoIP traffic helps detect and respond to suspicious activities in real-time. Network monitoring tools can identify anomalies and potential security threats, allowing quick intervention. Monitoring also helps identify patterns that could indicate an ongoing attack.
6. Implement Access Controls
Access controls are crucial for restricting unauthorized access to VoIP systems. Role-based access control (RBAC) ensures that users have access only to the resources they must perform their duties. Limiting access reduces the risk of internal threats and unauthorized usage.
7. Conduct Regular Security Audits
Regular security audits help identify vulnerabilities and areas for improvement in VoIP systems. They involve reviewing system configurations, access controls, and overall security practices. Audits offer valuable insights into security measures and help address potential weaknesses.
8. Educate and Train Employees
Human error is a major factor in security breaches. Educating and training employees on VoIP security best practices can reduce the risk of breaches. Training should cover several topics such as recognizing phishing attempts, proper password management, and safe usage of VoIP systems.
9. Implement Redundancy and Failover Mechanisms
Redundancy and failover mechanisms ensure VoIP services remain operational during an attack or system failure. Implementing backup systems and redundant network paths helps maintain service continuity and minimizes downtime.
10. Partner with Secure VoIP Providers
Choosing a secure VoIP provider is crucial for ensuring the overall security of your communication systems. Providers that prioritize security and offer robust security features can significantly enhance your VoIP infrastructure’s security posture.
VoIP security is a multifaceted challenge that requires a comprehensive approach. Understanding the role of SBCs in VoIP security and partnering with secure VoIP providers are also crucial steps in protecting communication systems from cyber threats.
🚨 VoIP security isn’t optional—it’s mission critical. Let’s lock it down.
Ensuring Comprehensive Security for Your VoIP Developers
Securing your VoIP infrastructure is a critical task that requires a comprehensive and proactive approach. By implementing the security enhancements outlined in this guide, you can protect your VoIP SBC and ensure your VoIP communications’ integrity, confidentiality, and availability. As a developer, staying vigilant and informed about the security threats and best practices is vital to maintaining a secure VoIP environment. Embrace these strategies by connecting with hire VoIP Developers to fortify your systems and provide users with a safe, reliable communication solution.